 New challenging to detect malware assaults discovered on Linux-based mostly units
[ad_1]
New challenging to detect malware assaults discovered on Linux-based mostly units
[ad_1]
Why it issues: Earlier this 7 days, researchers from Blackberry and Intezer released info on a difficult-to-detect Linux malware targeting Latin American monetary institutions. Known as Symbiote, the threat provides unauthorized buyers with the skill to harvest credentials or think remote entry to the concentrate on device. When infected, all malware is hidden and rendered undetectable.
Intezer's Joakim Kennedy and the Blackberry Exploration and Intelligence Team learned that the menace presents as a shared object library (SO) instead than a usual executable file that people should run to infect a host. After contaminated, the SO is loaded into presently functioning procedures on the goal machine.
The infected computer systems provide danger actors with the skill to harvest credentials, leverage distant accessibility capabilities, and execute commands with usually unauthorized elevated privileges. The malware is loaded in advance of any other shared objects by using the LD_PRELOAD directive, allowing for it to keep away from detection. Becoming loaded initial also makes it possible for the malware to leverage other loaded library files.
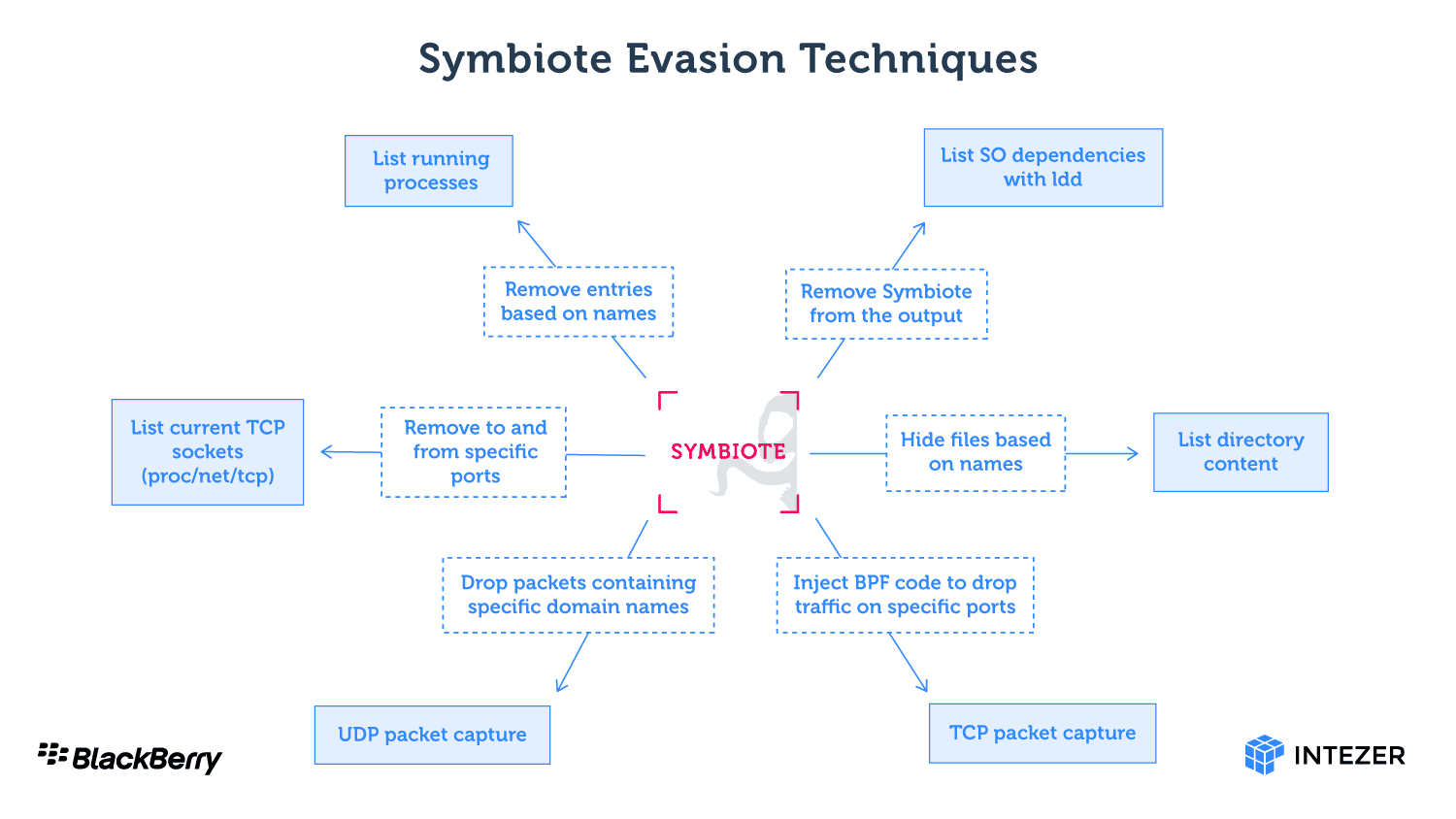
In addition to the steps described earlier mentioned, Symbiote can hide the contaminated machine's community exercise by making distinct temp data files, hijacking infected packet filtering bytecode, or filtering UDP website traffic utilizing unique bundle seize features. The Blackberry and Intezer blogs provide in-depth explanations of each and every system if you are into the technological specifics.
The crew 1st detected the menace in Latin American-centered financial institutions in 2021. Given that then, the workforce has identified that the malware shares no code with any other regarded malware, classifying it as a completely new malware threat to Linux running systems. Though the new danger is made to be challenging to discover, admins can use community telemetry to detect anomalous DNS requests. Security analysts and technique administrators can also use statically connected antivirus (AV) and endpoint detection and response (EDR) instruments to make sure userland stage rootkits do not infect target devices.
[ad_2]




0 comments:
Post a Comment