 Routers from Asus, Netgear, and Cisco are currently being focused by a innovative malware campaign
[ad_1]
Routers from Asus, Netgear, and Cisco are currently being focused by a innovative malware campaign
[ad_1]
Why it issues: The change to a hybrid perform design with many staff members working from house has opened up a new avenue for malicious actors. Safety scientists alert that a innovative malware campaign has been targeting North American and European dwelling and tiny business networks by means of router malware that has mostly gone unnoticed until finally not too long ago.
Last year, cyberattacks in opposition to company networks achieved record-environment levels in phrases of frequency and measurement, generally simply because of the Log4J vulnerability that was remaining unpatched by several corporations for numerous months. Earlier this month, a new and challenging-to-detect malware was identified on Linux-primarily based units that had been thieving credentials and enabling remote obtain for destructive actors.
In a identical vein, a new stealthy remote obtain trojan dubbed ZuoRAT has been detected by security researchers at Lumen Black Lotus Labs. The group that identified the new menace thinks it has been infecting a huge vary of property and compact business office (SOHO) routers throughout Europe and North The usa with malware that can consider manage of units operating Windows, Linux, or macOS.
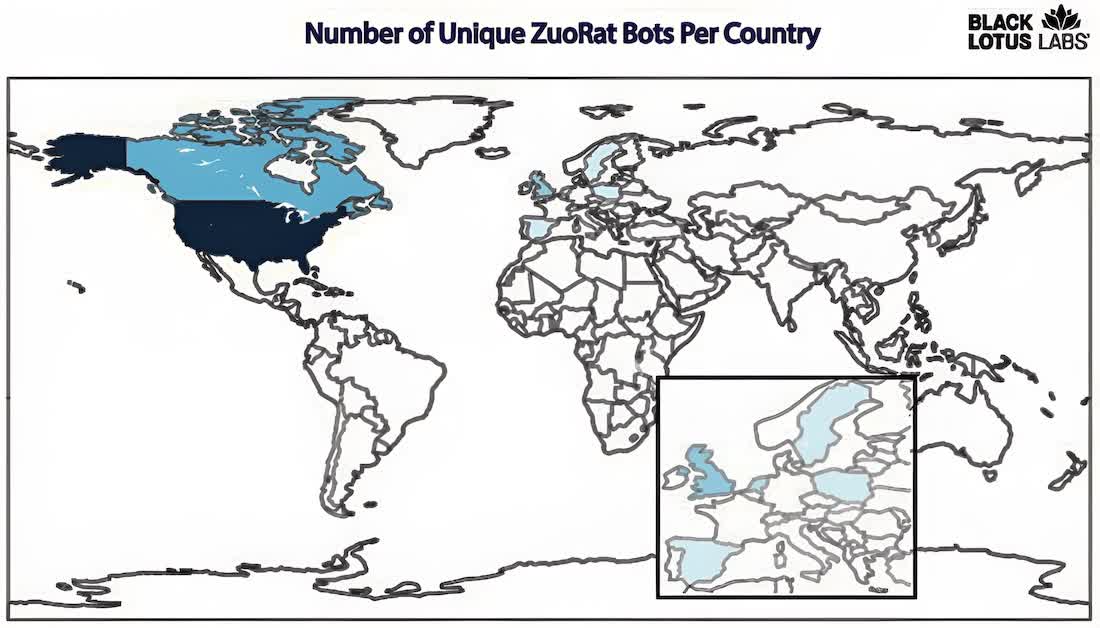
This has been likely on because at minimum December 2020, and ZuoRAT is thought to be aspect of a much broader malware marketing campaign that took gain of the unexpected and huge change to distant operate and review. The destructive actors chose to attack client-grade routers with exploitable firmware that is rarely monitored and patched, if at any time.
Black Lotus Labs researchers claim they've recognized at least 80 targets so significantly, and located ZuoRAT to be amazingly innovative for malware that is intended to compromise SOHO routers sold by Asus, Netgear, DrayTek, and Cisco.
The malware marketing campaign leverages no less than 4 diverse pieces of malicious code, and ZuoRAT is worryingly related to other custom made-built malware published for the MIPS architecture these as the just one guiding the infamous Mirai botnet of yesteryear.
After ZuoRAT would make its way into a router, the malicious actors can use DNS and HTTP hijacking to install further parts of malware dubbed Beacon and GoBeacon, as well as the commonly-applied Cobalt Strike hacking instrument.
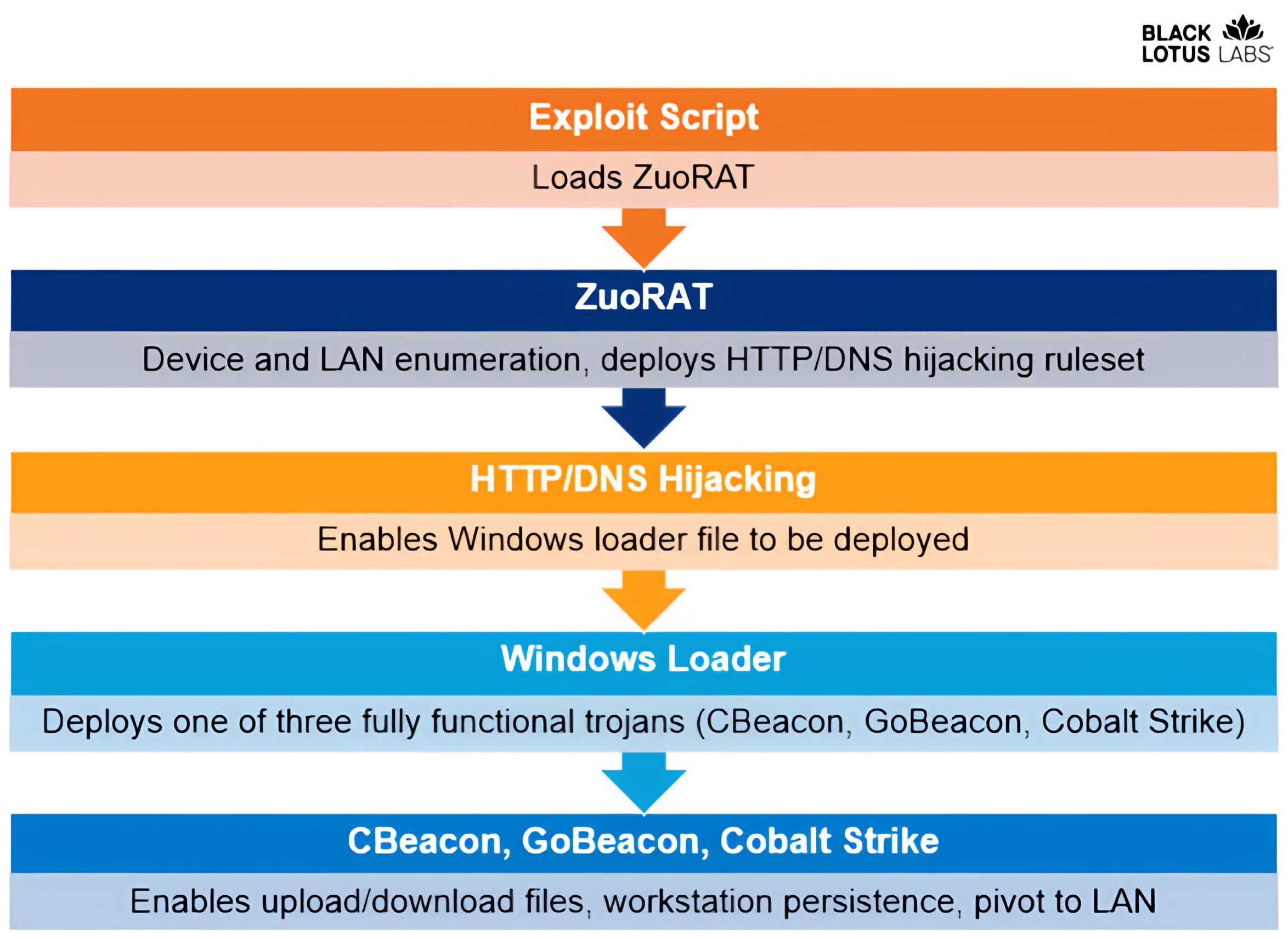
Researchers spelled out the campaign is aimed at various US and Western European organizations and the attackers have absent to extreme lengths to cover their action as a result of obfuscated, multistage C2 infrastructure. And whilst it is really only a suspicion at this issue, the analyzed info suggests the attackers may possibly be functioning in the Chinese province of Xiancheng working with details heart infrastructure from Tencent and Alibaba's Yuque collaboration software.
The excellent information is that router malware like ZuoRAT can be flushed out with a uncomplicated reboot of the contaminated system due to the fact that would wipe its files which reside in a short term folder. A manufacturing unit reset would be even far better, but if the infected units also incorporate the other items of malware they will not be as effortless to take out.
Security analysts and technique administrators can find a lot more information about the technical facets of the ZuoRAT campaign, including indicators of compromise and attainable prevention applications, by examining the full report and consulting the Black Lotus Labs GitHub.
[ad_2]




0 comments:
Post a Comment