 Stealthy backdoor has been concentrating on Microsoft Exchange servers all-around the entire world
[ad_1]
Stealthy backdoor has been concentrating on Microsoft Exchange servers all-around the entire world
[ad_1]
A hot potato: If just one essential much more indication that the stability of Microsoft Exchange servers nevertheless appears to be like Swiss cheese, a threat actor known as Gelsemium has provided a single. Protection scientists at Kaspersky consider the team has been applying stealthy malware dubbed SessionManager to attack the server infrastructure of public organizations globally for a lot more than a year.
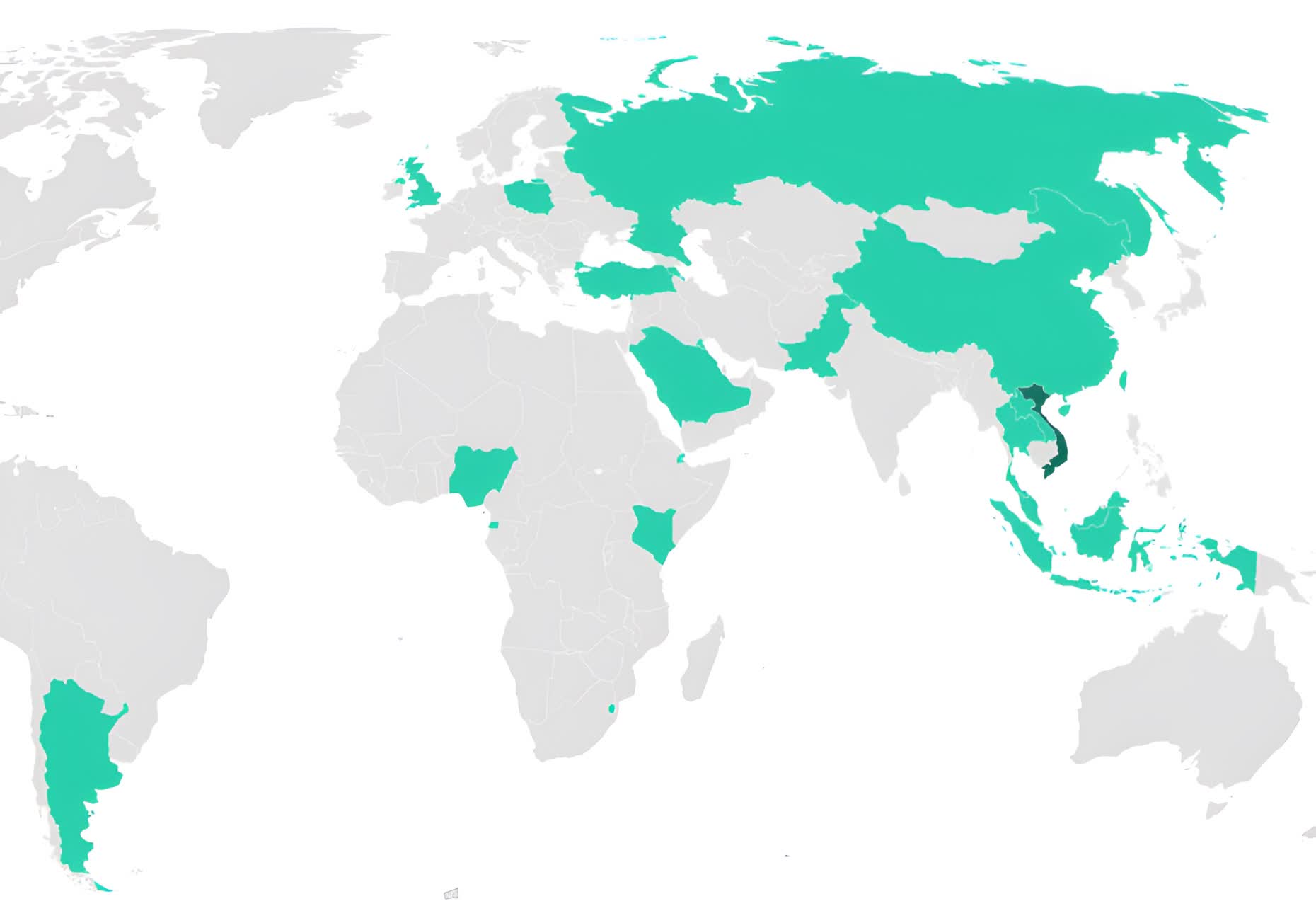
On Thursday, Kaspersky scientists published a stressing report relating to a new, challenging-to-detect backdoor that targets Exchange servers utilised by federal government and clinical establishments, military businesses, and NGOs in many countries. The malware, dubbed SessionManager, was very first spotted in early 2022.
At the time, some of the malware samples noticed by analysts were not receiving flagged by lots of well-known on-line file scanning products and services. In addition, the SessionManager infection persists in about 90 per cent of the targeted corporations.
The danger actors powering SessionManager have been working with it for the earlier 15 months. Kaspersky suspects a hacking team called Gelsemium is dependable for the attacks mainly because the hacking patterns fit the group's MO. Nevertheless, analysts can not verify Gelsemium is the culprit.
The malware uses powerful malicious native-code modules penned for Microsoft's Online Information and facts Expert services (IIS) net server computer software. When set up, they will respond to special HTTP requests to accumulate delicate info. Attackers can also choose entire command around the servers, deploy extra hacking applications, and use them for other malicious reasons.
Interestingly, the system of putting in SessionManager depends on exploiting a set of vulnerabilities collectively known as ProxyLogon (CVE-2021-26855). Previous yr, Microsoft said that well above 90 percent of Exchange servers had been patched or mitigated, but that nevertheless left numerous presently-compromised servers at threat.
The disinfection method is pretty complex, but Kaspersky scientists have presented a couple tips on preserving your group against threats like SessionManager. You can also consult Securelist for a lot more pertinent info on how SessionManager operates and indicators of compromise.
[ad_2]




0 comments:
Post a Comment