 This security guru is banishing spammers to a hilarious 'password purgatory'
[ad_1]
This security guru is banishing spammers to a hilarious 'password purgatory'
[ad_1]
No matter whether it’s John Wick or The Depend of Monte Cristo, we all enjoy a good revenge tale. Correct now, my present-day beloved is a healthful nerdy tale informed by Troy Hunt.
You possible previously know Hunt as the drive powering Have I Been Pwned, an priceless security resource for us normies on the web. The internet site tells you if your electronic mail deal with or cellular phone range has been located in knowledge breaches, and if you’re so inclined, lets you sign up for notifications ought to your information turn out to be exposed later on on.
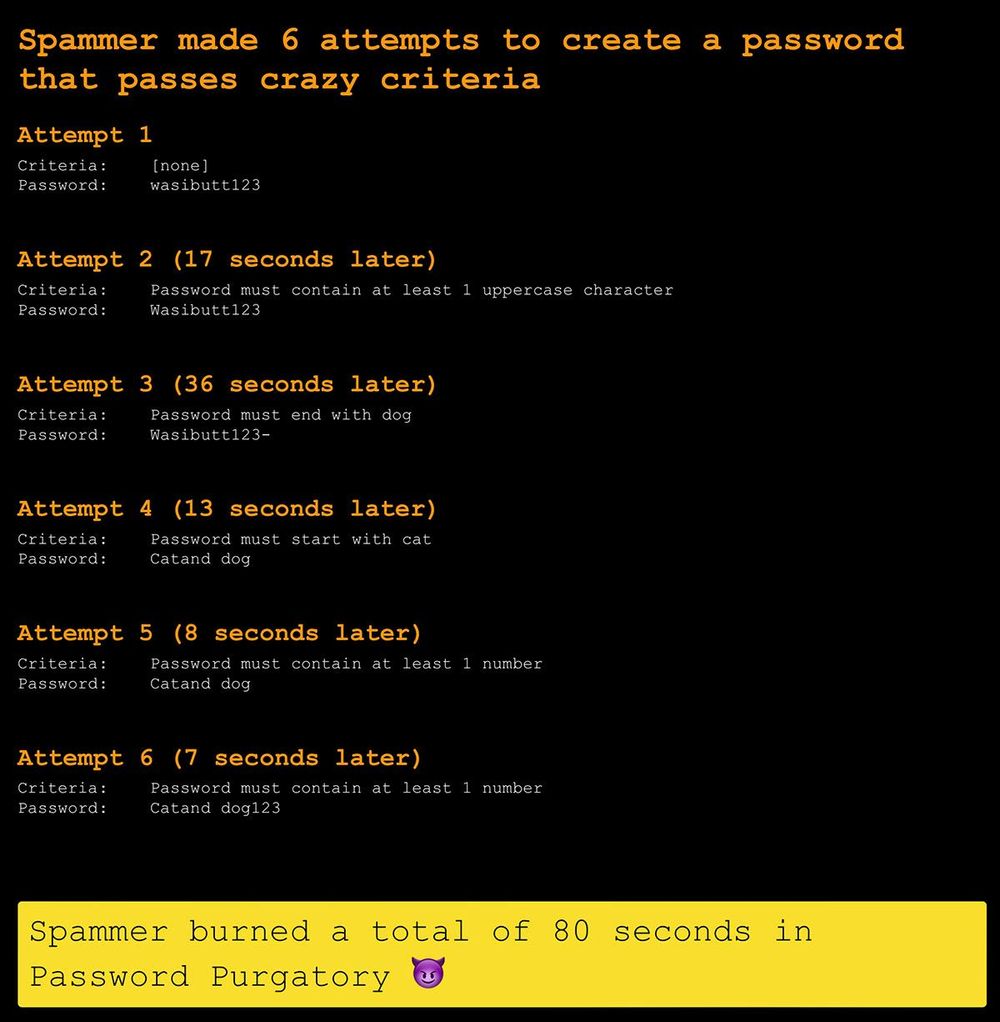
But he also files his different aspect initiatives. His hottest: Dishing a very little return soreness to spammers for stealing time from him. The punishment involves sending them to what he calls “password purgatory.”
Employing a concoction that blends Microsoft Power Automate and CloudFlare applications, Hunt lures spammers into imagining they’ve found an effortless mark. All they have to do is go to a simple registration sort on his web-site, make a username and password, and then financial gain off the sweet, simple web page backlinks. Except…he’s just toying with them.
Troy Hunt / troyhunt.com
The purpose? To see how very long those who choose the bait endure the increasingly hilarious password necessities. He’s also currently being variety plenty of to share the outcomes with the rest of us for our amusement. I like to consider of these as a application engineer’s edition of people glitter bomb movies on YouTube—the types where porch pirates are subjected to a surprising, unexpected explosion of glitter right after thieving the package deal.
It’s gratifying. And entertaining.
You can check out the comprehensive particulars of how Hunt spun alongside one another this splendidly evil form of purgatory in his web site post—which contains a connection to a Github repository with all the code he made use of. If you are so inclined, you way too can set spammers by the ringer.
[ad_2]




0 comments:
Post a Comment