 Chaos: a powerful malware infecting many systems and architectures
[ad_1]
Chaos: a powerful malware infecting many systems and architectures
[ad_1]
TLDR: A impressive malware capable of infecting a number of systems and CPU architectures is creating wonderful strides in Europe and elsewhere. The Chaos menace spreads by means of Windows and Linux, and is made to execute remotely-issued commands by cyber-criminals.
Chaos is a novel malware written in the Go programming language with quite unique capabilities. Learned and analyzed by Black Lotus Labs, the research arm of safety business Lumen, the new menace can infect a plethora of computing platforms equally on the software program and hardware entrance. There are much more than a hundred contaminated equipment as of now, a destructive network that could be leveraged to spread other threats and malware strains as very well.
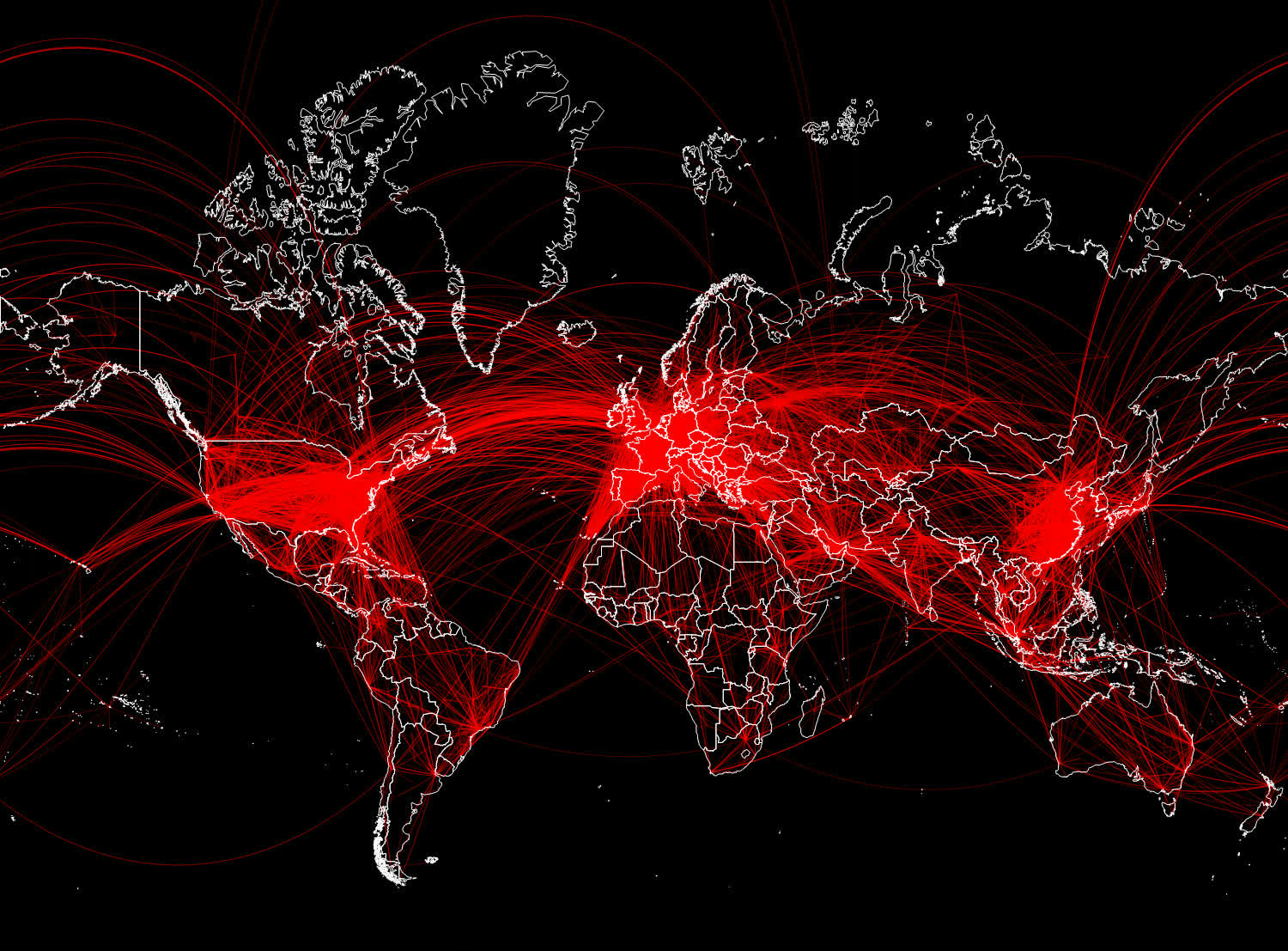
Black Lotus scientists named the new malware "Chaos" as the phrase has been regularly employed in the code for operate names, certificates and file names. Chaos began to emerge in April, the researchers say, and now there are much more than 111 one of a kind IPs belonging to contaminated devices. Chaos is a really versatile danger, as the aforementioned products consist of regular Personal computer units, tiny workplace routers and big enterprise bins.
Chaos is in fact intended to operate on several computing architectures, including traditional Computer system processors (i386), ARM, MIPS and PowerPC CPUs. On the software aspect, Chaos can run on Windows, Linux and FreeBSD as well. Compared with ransomware threats and botnets that hire spam strategies to unfold the an infection, Chaos can distribute by exploiting known CVE vulnerabilities and compromised SSH keys.
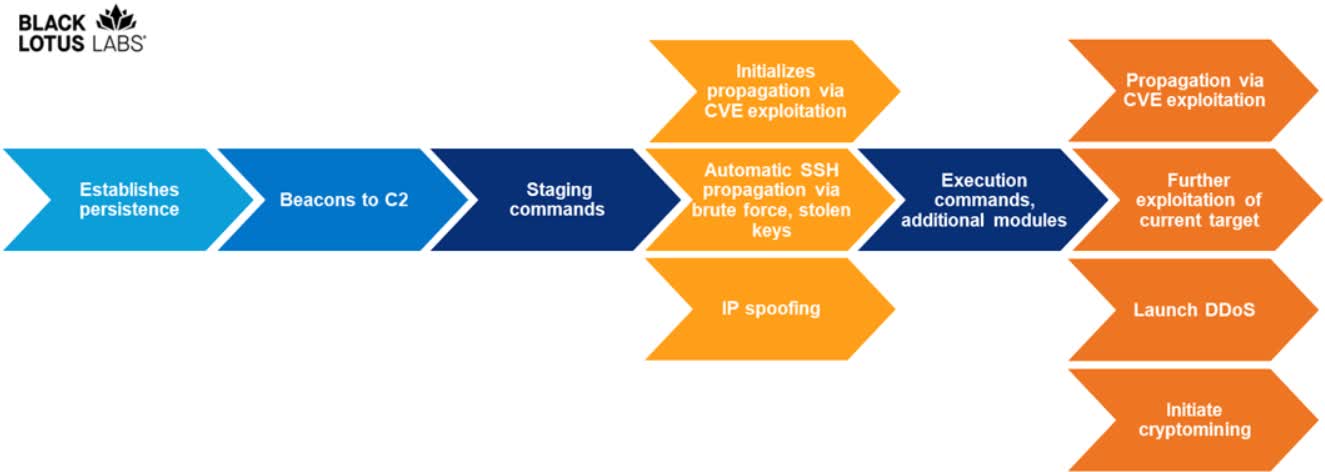
The samples analyzed by Black Lotus contained flaws impacting Huawei (CVE-2017-17215) and Zyxel (CVE-2022-30525) own firewalls other than other, very well-recognised CVEs. Following infecting a machine, Chaos can use its different capabilities like enumerating all products connected to a community, running distant shells to execute destructive commands and loading added modules. According to researchers, the malware's complexity is evidence that Chaos was made by a "cybercriminal actor that is cultivating a community of contaminated units to leverage for first access, DDoS attacks and crypto mining."
Black Lotus says Chaos is probably an offspring of Kaiji, a previously recognized botnet targeting Linux (i386) servers for undertaking DDoS assaults. The malware is a great deal extra developed now, contemplating its new strong capabilities and the capability to run on Home windows and FreeBSD equipment in addition to Linux. The compromised IPs recognized by the security enterprise are primarily situated in Europe, with more compact infection places in North and South The united states and in the Asia-Pacific location.
In concluding their assessment, the researchers advise a couple of very best practices to keep away from becoming infected by a complicated and hazardous risk like Chaos. Patch management for newly discovered vulnerabilities must be "powerful," the authors say, while SOHO routers need normal reboot cycles (other than installing the most current firmware upgrades) as most router malware can't endure a reboot. On top of that, remote workers must adjust the default passwords and disable distant root entry on equipment that will not need it.
[ad_2]




0 comments:
Post a Comment