 BlackLotus, the new UEFI rootkit that helps make security researchers worry
[ad_1]
BlackLotus, the new UEFI rootkit that helps make security researchers worry
[ad_1]
Why it issues: "BlackLotus" is becoming supplied on underground message boards as an all-impressive firmware rootkit, capable of surviving any removing exertion and bypassing the most advanced Windows protections. If true malware samples can demonstrate the give is genuine, of class.
A new effective UEFI rootkit is reportedly up for sale on underground discussion boards, supplying highly developed assault attributes that had been earlier available only to intelligence companies and condition-backed danger groups. BlackLotus, as the unidentified vendor has named the malware, is a firmware rootkit that can bypass Home windows protections to operate malicious code at the least expensive stage of the x86 architecture security rings.
In accordance to stability researchers that noticed the BlackLotus adverts on crimeware community forums, a solitary rootkit person license expenses up to $5,000, when a subsequent code rebuild is "just" $200. Looking at the capabilities listed by the vendor, even shelling out $5,000 could be noticed a true discount for cyber-criminals and black hat hackers around the world.
As summarized by safety researcher Scott Scheferman, BlackLotus is written in Assembly and C and weighs 80 kilobytes (just all over 81,920 bytes in sizing) when it can be vendor impartial. The rootkit has anti-VM, anti-debug and code obfuscation capabilities to block or hinder evaluation tries, provides an "agent security" at kernel stage (ring ) for persistence in the UEFI firmware, and it will come with a thoroughly featured put in guide and FAQ.
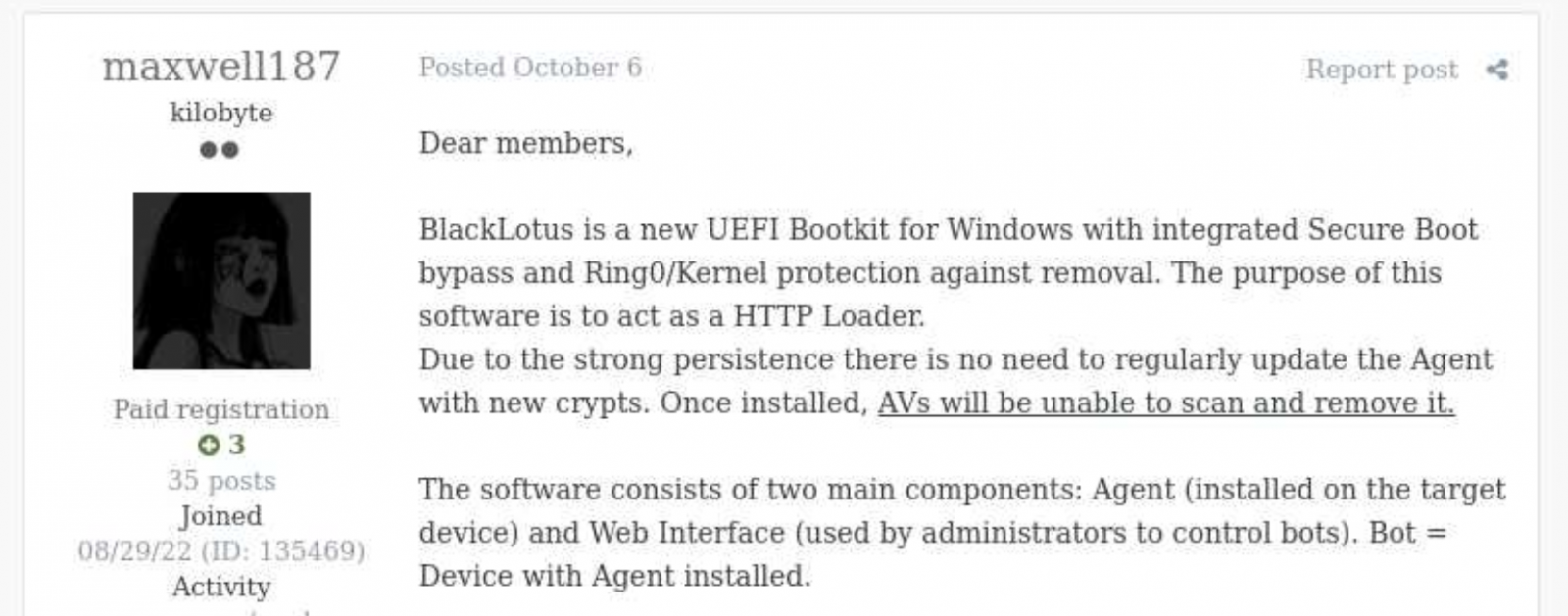
Like any other appropriate rootkit, BlackLotus is loaded in the extremely very first stages of the boot course of action ahead of the Windows startup stage. The malware can allegedly bypass quite a few Home windows security protections including Secure Boot, UAC, BitLocker, HVCI and Windows Defender, even though presenting the capacity to load unsigned drivers. Other advanced attributes of the malware contain a entirely showcased file transfer manner, and a "vulnerable signed bootloader" that cannot be invalidated with no affecting hundreds of bootloader nevertheless in use nowadays.
Scott Scheferman highlights the threat BlackLotus can pose for modern day firmware-primarily based stability, making a menace level earlier out there only to superior-persistent threats (APT) by point out-sponsored teams like the Russian GRU or China's have APT 41 accessible to any person. The new UEFI rootkit could stand for a authentic leap forward for cyber-criminal offense in terms of ease of use, scalability, accessibility, persistence, evasion and destruction likely.
UEFI rootkits have been after regarded as to be really exceptional and specialized threats, but numerous discoveries in the past several many years have revealed a absolutely various scenario. As for BlackLotus, the security neighborhood will need to evaluate an real sample of the malware to determine if the advertised functions are real, if it truly is production prepared, or if it truly is just an elaborated fraud.
[ad_2]




0 comments:
Post a Comment