 3 essential protection lessons from the Uber hack
[ad_1]
3 essential protection lessons from the Uber hack
[ad_1]
Ridesharing support Uber admitted to a breach of its inside network late final 7 days, with the hacker purportedly getting accessibility to Uber’s source code, email, and other methods like Slack. The company then soon reassured the general public that no purchaser facts was compromised—a claim that not all security industry experts uncover plausible.
You should really of system continue to adjust your Uber account qualifications and confirm you’re not working with that previous password anyplace else it’s an quick and sensible precaution to take, as the company’s record includes masking up a main client facts breach for about a year. But which is not the important takeaway from this incident.
The hack is becoming described as the end result of social engineering—and overrode safety actions that involved two-variable authentication (2FA). An personnel with a compromised password was spammed with 2FA authentication requests, a person of which was at last accredited following the hacker posed as an Uber IT individual and contacted the personnel over Whatsapp.
This consequence doesn’t indicate pairing a sturdy, unique password with two-aspect authentication is not helpful. Only that social engineering is incredibly potent, preying on conveniently produced problems. In actuality, this most recent Uber breach highlights three crucial techniques you can improved safeguard on your own on-line.
1. Usually end and assume
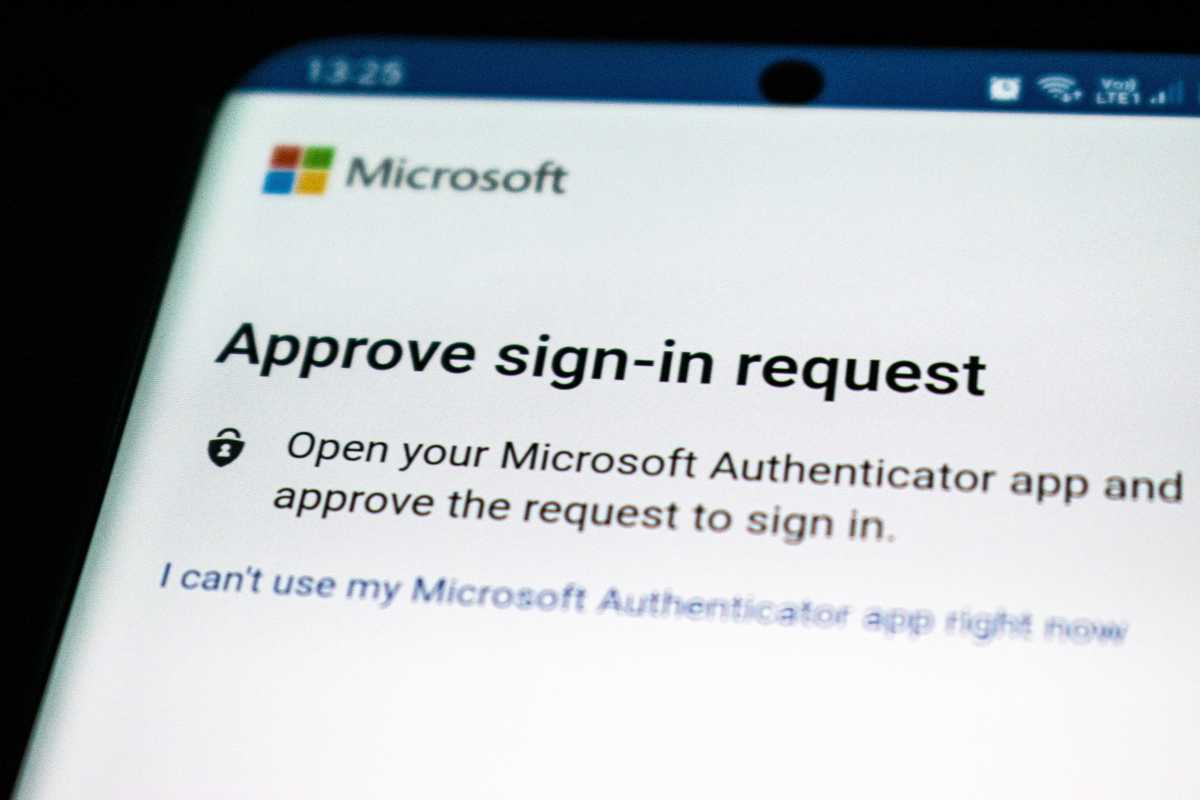
Ed Hardie / Unsplash
A password is your initial line of defense against unauthorized accessibility to your on the internet accounts. Two-element authentication is the next layer of defense, in situation your password turns into compromised.
If you pick a sort of 2FA that sends requests to your cellular phone or an application on your mobile phone, authorization requests ought to only pop up when you productively enter a password.
You. No one else. The web-site or application itself has method permissions to entry your account(s) and all the exercise you have carried out on them without the need of ever involving you. (So does your IT office for get the job done-associated accounts, for the document.)
You should really only see a 2FA authorization request arrive by means of when you are in the center of logging into an account. If not, you’ve bought a problem—especially if you are having all but spammed with multiple requests.
So your third and ultimate layer of protection is your sharp, lively brain. Be wary of surprising 2FA requests. They are absolutely fishy (that is, “phishy”).
2. Know who to belief
Markus Spiske / Pexels
Account access must be only obtainable to two entities: You and the organization jogging the web-site, support, or application. And as described earlier mentioned, that firm doesn’t require you to entry your account. Always rule out interaction requesting your password or two-issue information as fraudulent.
When you have obtained a two-factor authentication request out of the blue, that is your cue to connect with in reinforcements. Call the web-site or app’s customer provider immediately. You want to report the unauthorized use of your password, and receive guided guidance in resecuring your account.
(You may possibly be tempted to transform your password immediately—not a poor intuition, but you’ll usually will need to move a two-factor verify for it to go by if 2FA is lively. If you have only this one technique for 2FA, and your hacker is sending many requests to your phone, you could operate the chance of unintentionally approving your would-be hacker’s request alternatively of the 1 you generated.)
3. Choose a resilient form of 2FA

Yubico
The more easy your form of authentication, the less difficult to compromise. This axiom applies as substantially to two-component authentication as, say, password size.
Password duration receives talked over way far more generally, simply because it is the first line of defense and usually the only line of defense. Tech journalists and protection specialists usually sigh in reduction when folks use any type of 2FA at all. But two-factor authentication techniques change in how resistant they are to hacking and human error:
- Email and text message are straightforward and easy to recognize, and you can generally entry them from numerous products. Nevertheless, they also depend on unsecure interaction. These forms of accounts can be taken about by using social engineering, as well.
- Products (e.g., smartphones or tablets) and applications that obtain drive requests are an advancement more than e mail or textual content, and transferring the 2FA set up to a new system (when necessary) is generally effortless. But they are however weak towards human fallibility, like a oversight when swiping or tapping on a mobile phone monitor, or social engineering.
- Apps that you have to open manually to check out a 2FA code really should only be viewable to you—a significant moreover. On the other hand, this stage of stability only applies when codes are only accessible regionally on the system, not when saved and synced by using cloud storage. The draw back is that if you really do not again up your setup, restoring access to your 2FA codes can be a royal suffering.
- Hardware tokens are completely unbiased physical merchandise that can crank out and display a 2FA code for use, or tackle the 2FA authorization seamlessly via a USB port or a wireless relationship (NFC or Bluetooth). As you can imagine, these are incredibly safe, but operate the possibility of becoming dropped. (You will typically need more than just one for protection.)
In quick, if you know you’re very likely to be extra inclined to social engineering (or are at possibility for a lot more tries at social engineering), pick a process that covers your rear if you have an off working day. Just be absolutely sure to shield by yourself in opposition to logistical headaches, too—which are likelier with additional safe types of 2FA. For even a lot more safety ideas, be sure to read our guide to 5 uncomplicated duties that supercharge your safety.
[ad_2]




0 comments:
Post a Comment