 How to use the new Passkeys on your Iphone, iPad, and Mac
[ad_1]
How to use the new Passkeys on your Iphone, iPad, and Mac
[ad_1]
“Passkey” is Apple’s title for a simplified login course of action to internet sites that comes in its entire glory afterwards this yr with macOS 13 Ventura, iOS 16, and iPadOS 16. A passkey depends on broadly supported business criteria to let you carry out an encrypted login with just about no energy on your section after the first set up.
You can test a passkey without the need of installing the community betas of these approaching running systems, as Apple created passkey assist in a preview variety into Safari throughout all its working methods in iOS 15, iPadOS 15, and Safari 15 with macOS 12 Monterey.
With the entire release of passkeys in a couple of months or months, and Google and Microsoft’s declared support for appropriate technological know-how, you are likely to see alternatives to add a passkey login at several web-sites this slide.
Here’s how the course of action performs.
Enroll at a web page
A passkey includes a paired established of encryption keys, recognized usually as general public-crucial cryptography. When you check out a server that supports WebAuthn (the know-how essential to acknowledge, shop, and interact with a passkey), your browser will existing the community critical of the encryption pair. The public essential just cannot be made use of for login but fairly to demonstrate your identification: you have the non-public key, which is established on your product and under no circumstances leaves it for a login.
To enroll, you visit a web site that presents passkey support. A website could possibly condition it supports passkeys generically, say that it has WebAuthn help, or declare that it is FIDO2, CTAP, or “multi-system FIDO credential” appropriate. All of all those terms ought to mean you can use an Apple (or Google or Microsoft) passkey as your login credential. (FIDO2 is the identify presented by the FIDO Alliance trade group, a important section of earning passkeys and WebAuthn take place, and which Apple, Microsoft, and Google are customers of.)
The procedure will do the job really likewise to when you enroll at a site for two-issue authentication (2FA) or if you have earlier used a hardware vital for WebAuthn, like those produced by Yubico:
- Log in applying your current username and password.
- The web site may possibly prompt you for more verification. This may possibly be a hyperlink despatched through e-mail, a texted code, or a prompt for a 2FA acknowledgment with a code or by means of an application you presently have set up on your Apple iphone or iPad.
- The site’s stability portion lets you opt for to use a passkey or a single of the alternate names previously mentioned.
- The world-wide-web server pushes a ask for to your browser to deliver encryption facts.
- You are prompted to approve this request with Contact ID, Face ID, or your device password, based on what is readily available and enabled.
- If you successfully validate your identification, your product generates the public/non-public important pair. The non-public critical is stored on your unit and never ever despatched to the distant site.
- Your browser sends the public crucial along with a cryptographically signed message that the server can validate making use of the presented general public essential: only anyone whose machine retains the non-public key can create a verifiable concept.
- The world-wide-web server retailers your community important for your foreseeable future logins.
Setting up a passkey login may disable 2FA on your account or enable you to opt for a passkey login as a substitute of a 2FA pathway. A passkey presents evidence of possession of both equally a top secret and the product on which it is stored, efficiently two variables. (Some greater-protection web sites and expert services may perhaps even now require 2FA in its place of or in addition to a passkey.)
You can see the passkey course of action at get the job done with some of the fundamental technical pieces exposed at Webauthn.me, a web page built by Auth0, a service provider of authentication providers. Some generation web sites now present passkey-appropriate logins, but they’re rather couple of at the instant. You could established a Google or Dropbox account to use a “security key” and use a passkey in its place. See below for my knowledge with that.
Log in with a passkey
At an enrolled web page, you can use a saved passkey the subsequent time you need to have to log in. You may have observed that many internet websites have begun to break up the consumer identify or account e-mail submission from a password submission–that seems to be prep for passkeys.
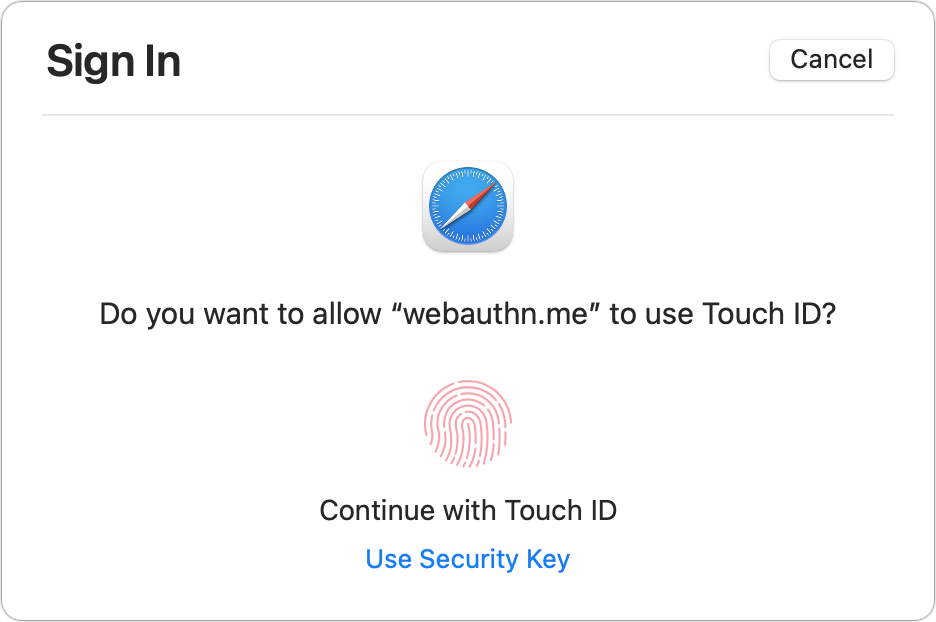
With a web page entirely ready for passkeys, you’ll faucet or click in a username or account email area and be prompted by Safari to validate a passkey login. In some scenarios, Safari could to start with request you if you want to allow for Contact ID or “security key” logins on the web site click Allow to carry on. Then you can authenticate by using Touch ID, Deal with ID, or your unit password just as through enrollment. Which is it! Employing the Webauthn.me site pointed out over, you can take a look at this in Stage 4 of its process.
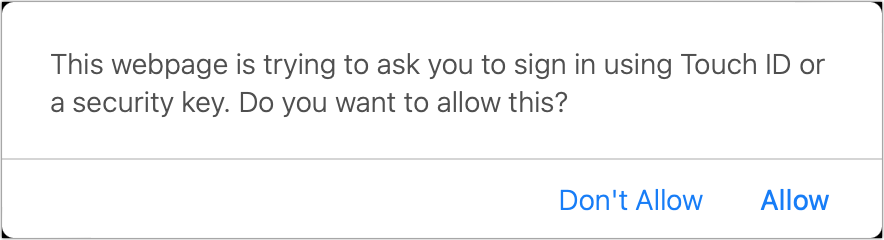
With some web pages that have WebAuthn assist but are not still thoroughly aligned with the simplified passkey approach, you could be prompted to conduct a regular user identify and password login in advance of the site initiates the sequence that asks your browser for a passkey.
I was capable to enroll with a passkey at Dropbox by picking out the Security Essential possibility and following the prompts in Safari for macOS. (Whilst logged into Dropbox via Safari, simply click your avatar in the upper-correct corner, simply click the Security connection, and click on Insert next to “Security keys.” When it asks if you have inserted the critical, validate you have.)
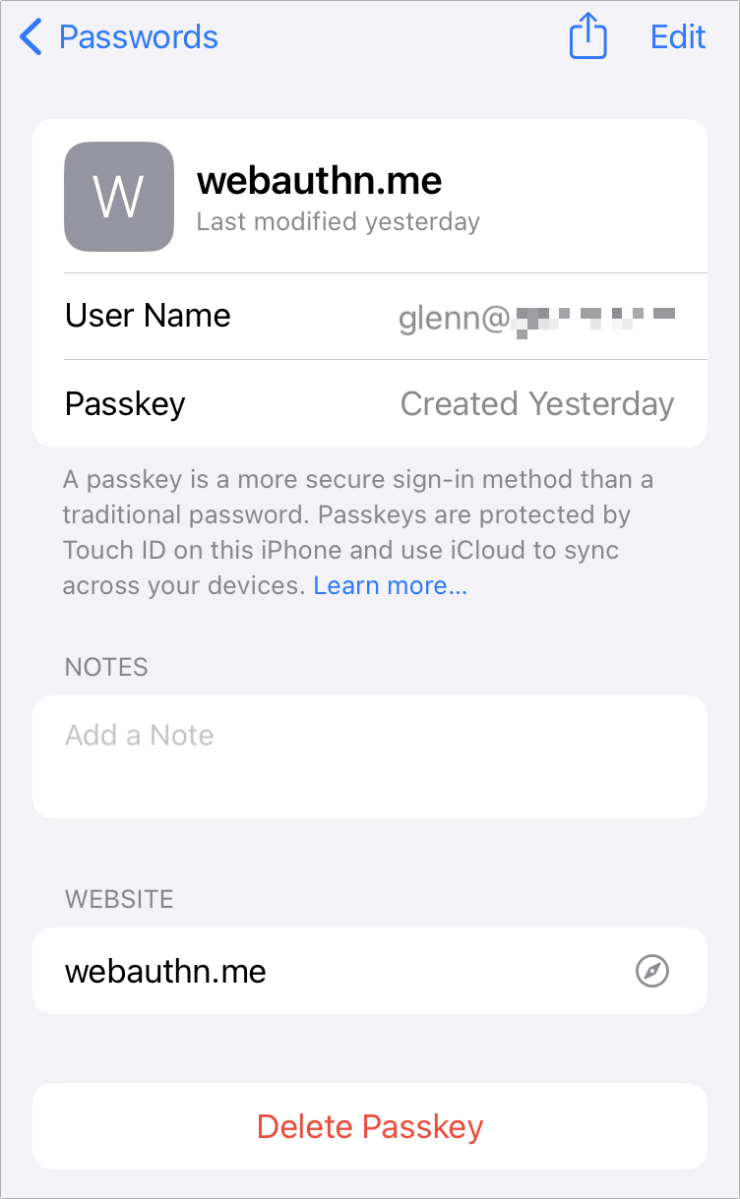
Subsequent logins labored in Safari for macOS but not in Safari for iOS, in all probability for the reason that of a absence of iCloud Keychain sync assist prior to the release of the new functioning devices. In iOS 16, iPadOS 15, and Ventura, with iCloud Keychain enabled, passkeys will sync and be shown in Settings > Passwords in iOS/iPadOS and Program Settings > Passwords in Ventura.
Apple will permit you share passkeys with other Apple people by securely sending them in excess of AirDrop. This will share the two the general public and private key and give folks the same degree of account entry as if you experienced offered them the username, password, and two-component token for your account.
Login from other products
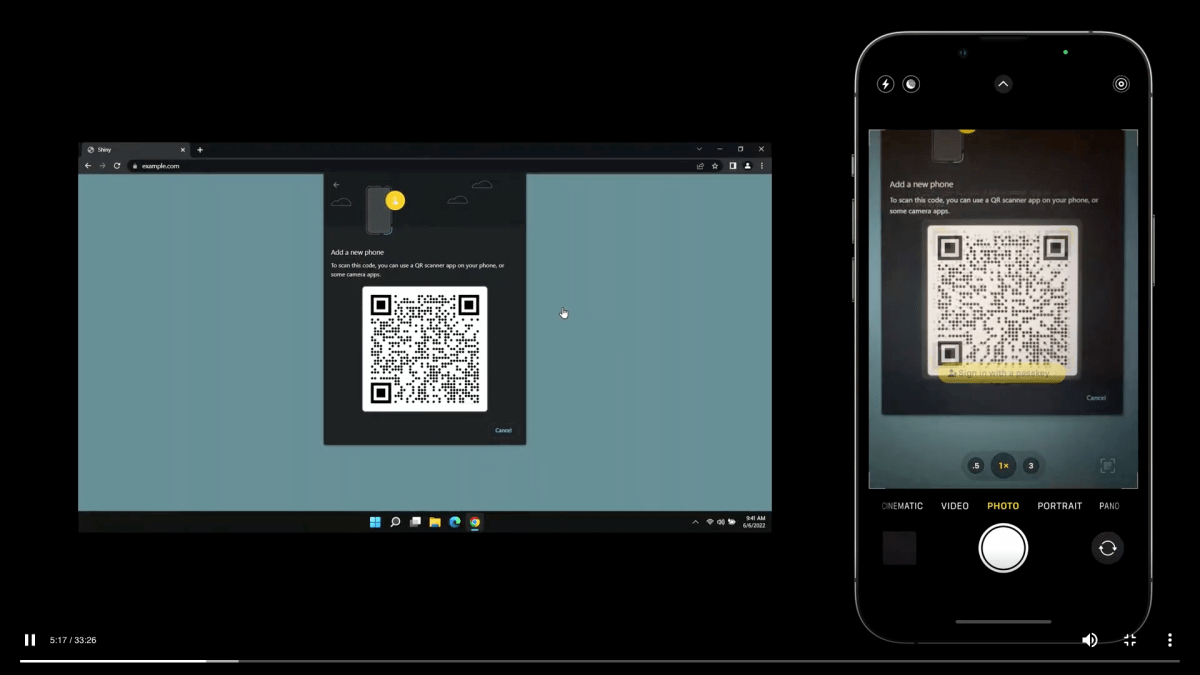
Some internet sites will let you specify a passkey login as your sole strategy to acquire access. So what if you’re hoping to log in from a product that doesn’t have your passkey stored, like a communal or relatives computer, a system at operate, or 1 you have entry to while traveling? Or you need to use a Windows procedure or Android mobile phone to entry a web-site thanks to features distinct to those people platforms? Apple shown a intelligent approach in its introduction to passkeys at the 2022 All over the world Developer Conference that requires a QR code and Bluetooth.
The approach works like this:
- On a product with an operating system or browser new sufficient to aid WebAuthn logins, when you enter your account identify at a site with which you use a passkey.
- The web page will query the browser for a passkey, and the browser will find it has none. You can then simply click to deliver a passkey by using a proxy, these types of as by clicking “Add a new phone.”
- The web page sends a question that results in the browser to display screen a QR Code.
- On your Apple iphone or iPad, you scan the QR Code and faucet the prompt “Sign in with a passkey.”
- On your product, click Go on and then approve the login with Touch ID, Facial area ID, or your product password.
- The browser displays you are logged in.
Apple
Through this approach, the product on which the QR Code is exhibited and your Iphone or iPad quietly build a connection via Bluetooth and trade critical information. This lets your machine get assurance that the login is occurring utilizing a piece of equipment that is nearby to protect against remote assaults, and the Bluetooth backchannel an encrypted channel individual from the browser connection, steering clear of phishing attacks that present phony logins.
Just after you have authenticated your login on that other gadget, your session proceeds as ordinary. Make absolutely sure and log out when you are finished to obvious the point out.
The foreseeable future is passkeys
The simplicity of passkeys hides the sophistication. For when, we get both of those simplicity, no overhead for controlling the system, and the optimum probable level of stability. Just about every login is distinctive, saved for you, and verified in both directions—by your gadget and by the site—to make sure only the man or woman with access to your device can log into the web site.
[ad_2]




0 comments:
Post a Comment